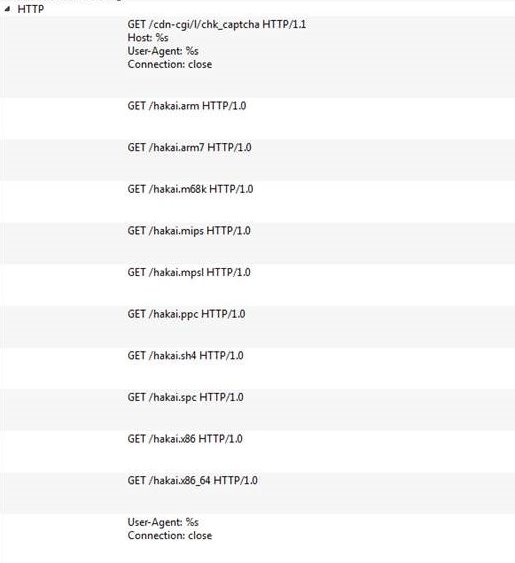
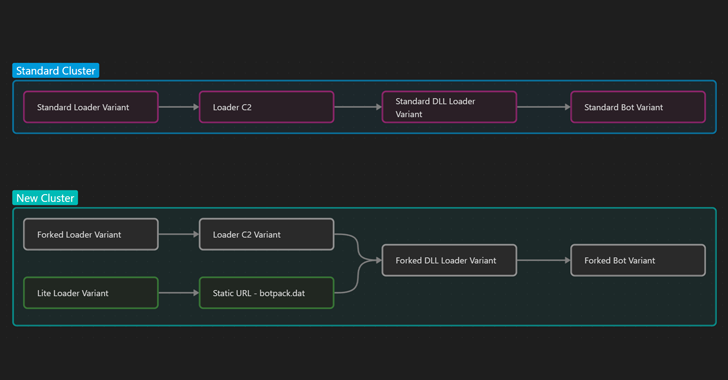
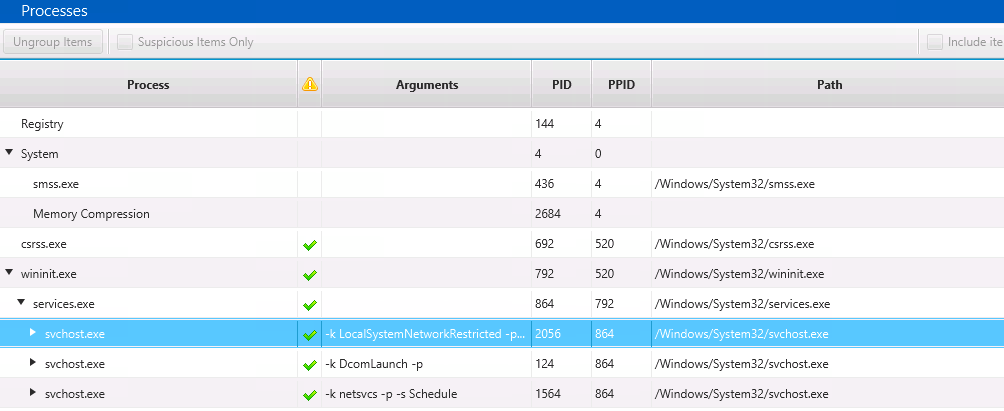
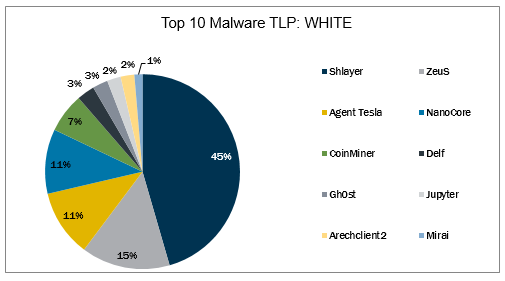
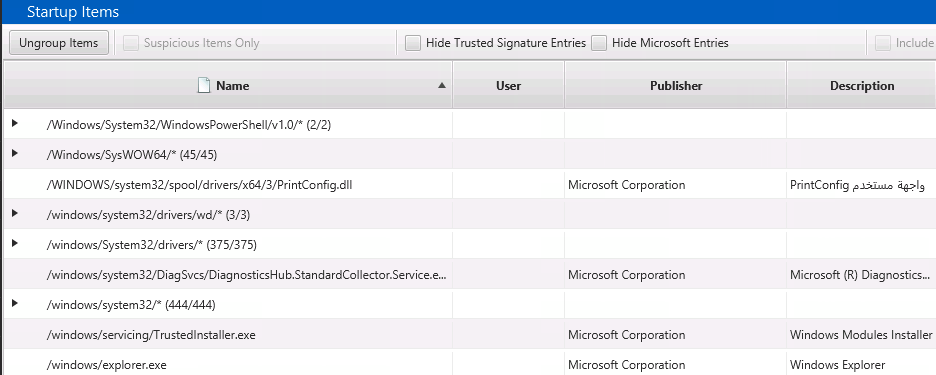
Malware Being Distributed by Disguising Itself as Icon of V3 Lite - Malware Analysis - Malware Analysis, News and Indicators
Antivirus NodeLab Lite - Malware and Adware Scan at Mac App Store downloads and cost estimates and app analyse by Softwario